IT-Security Management
ADWEKO supports financial service providers in the IT security management of their system landscape.
Every IT system landscape is subject to various risks, which increase with the growing importance of IT. In addition to internal risks, such as operating errors or misuse, the importance of external risks, such as hacker attacks, is growing. In order to take account of these growing risks, the regulator continues to develop the supervisory requirements and regularly redefines the supervisory focus areas.
Supervisory security management focuses on the protection of information that is processed by or with IT. The respective information is to be evaluated with regard to its protection requirement for the respective protection goals “confidentiality”, “integrity”, “availability” and “authenticity” and, depending on the protection goal, corresponding target measures for the protection of this information are to be implemented for the processing IT assets (applications, processes).
Development of a central Identity & Access Management
Implementation of a central authorization management tool with automatic Processes for granting and withdrawing authorizations, SoD management and recertification
Management of individual data processing
Definition of a life cycle for IDV with processes for identification, determination of protection requirements, development and replacement. Introduction of an IDV management system to ensure the completeness of the IDV inventory
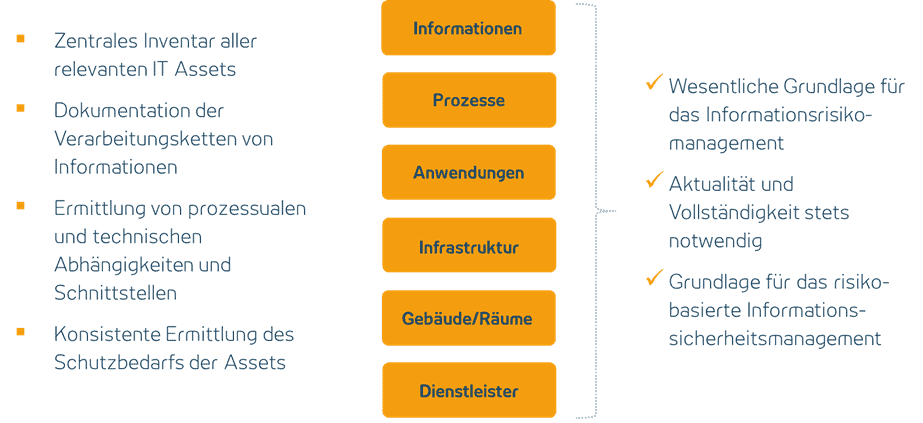
Structure of the information network
Establishment of a complete and always up-to-date information network as an overview of the IT assets (information, processes, applications, infrastructure, buildings, service providers) and for determining protection requirements
DIGITALE OPERATIVE RESILIENZ
FUTURE-PROOF IN THE DIGITAL WORLD
Within IT security management, there are numerous interactions between the individual disciplines, which is why we always take a holistic view of IT security management in our projects. Topics such as the management of administrators as part of the authorization management and their monitoring within the operational information security management with the help of the SIEM can hardly be separated from each other.
Setting up a comprehensive information security management system and monitoring its implementation and compliance as part of an internal control system that covers both 1st and 2nd line is an essential step towards sustainable IT security.
The information network is an essential building block in information security management, so the various IT assets and their interfaces and dependencies are documented here in order to determine the protection requirements of the IT assets. In addition to the classic consideration of the processed information objects for the protection objectives of confidentiality, integrity and authenticity and the supported processes for determining the availability requirements, cumulative risks and technical dependencies should also be taken into account when determining the protection requirements.
Depending on the protection requirements of the IT assets, target measures of different strengths should be defined on a risk basis and ideally described in a comprehensive catalogue of target measures.
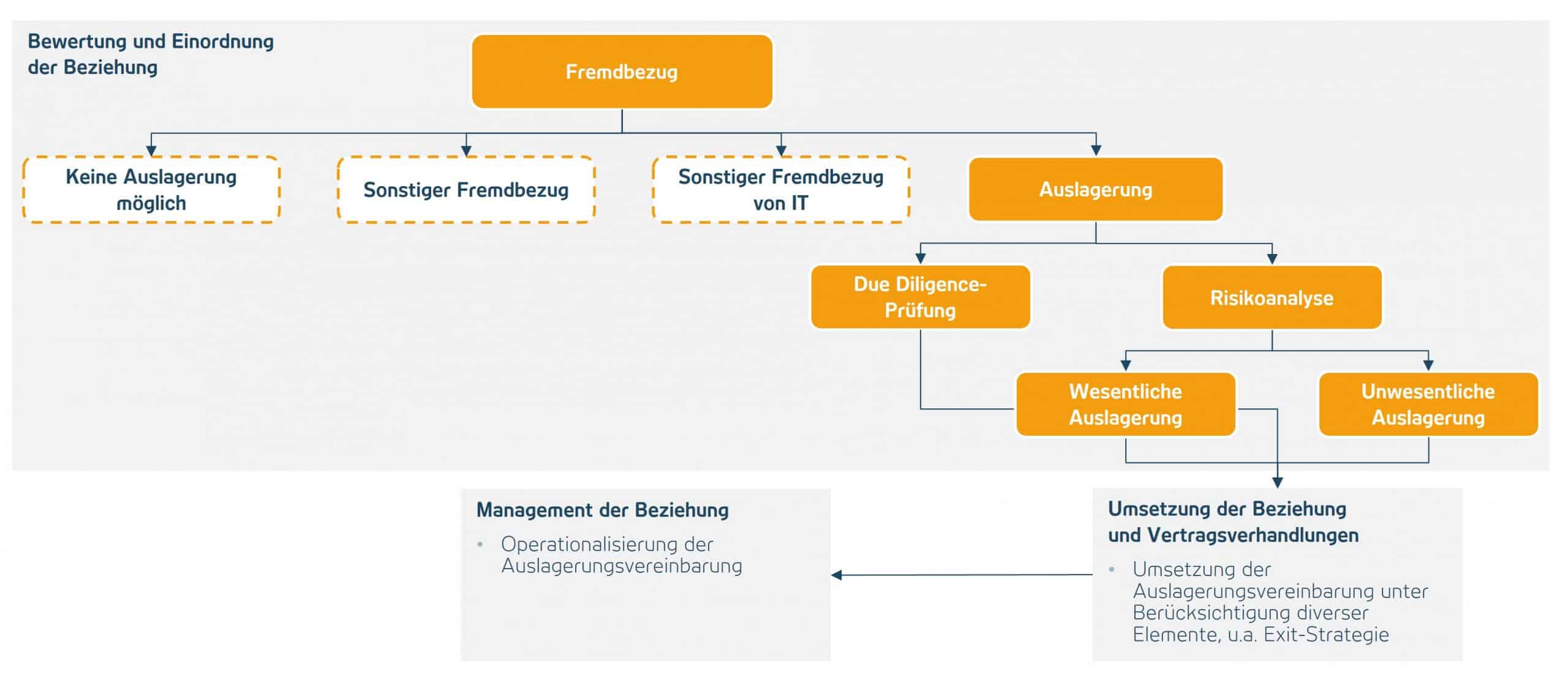
OUTSOURCING MANAGEMENT
Outsourcing management has the task of ensuring that the regulated institution has full responsibility for outsourced activities at all times. It must be informed about the outsourced activity as if it were performed within the institute itself. To ensure this, outsourcing management must be included in the purchasing process as early as possible. This means that every external purchase can be examined for its regulatory relevance. In addition, appropriate management of the service provider relationship and the resulting risks as well as a regular review of these are made possible.
The more significant the identified risks – and therefore the outsourcing – are, the stricter the supervisory requirements that need to be met. This applies not only to the contract with the service provider, but also to the operationalization of the relationship. For example, regular reports on the service provider’s performance must be obtained, reviewed and the results reported to management and, if necessary, to the supervisor.
Outsourcing management has close links to emergency management, information security and data protection. Cross-cutting issues also exist with the operational requirements of BAIT, VAIT, ZAIT and KAIT.
MORE ABOUT ITSM?
As ADWEKO we know the pitfalls in IT security management and we know how to design and implement measures on a project basis and how to continue them down the line afterwards.