Information security trends and threats
Information security has long since ceased to be a topic that only concerns IT. Over the last few years, attacks have multiplied and so have regulatory requirements related to information security. In addition, companies are also facing increasingly complex challenges such as artificial intelligence, working from home, which has become even more widespread thanks to Corona, and the ever-growing number of smart devices – the Internet of Things.
Internet of Things and 5G
What is the Internet of Things?
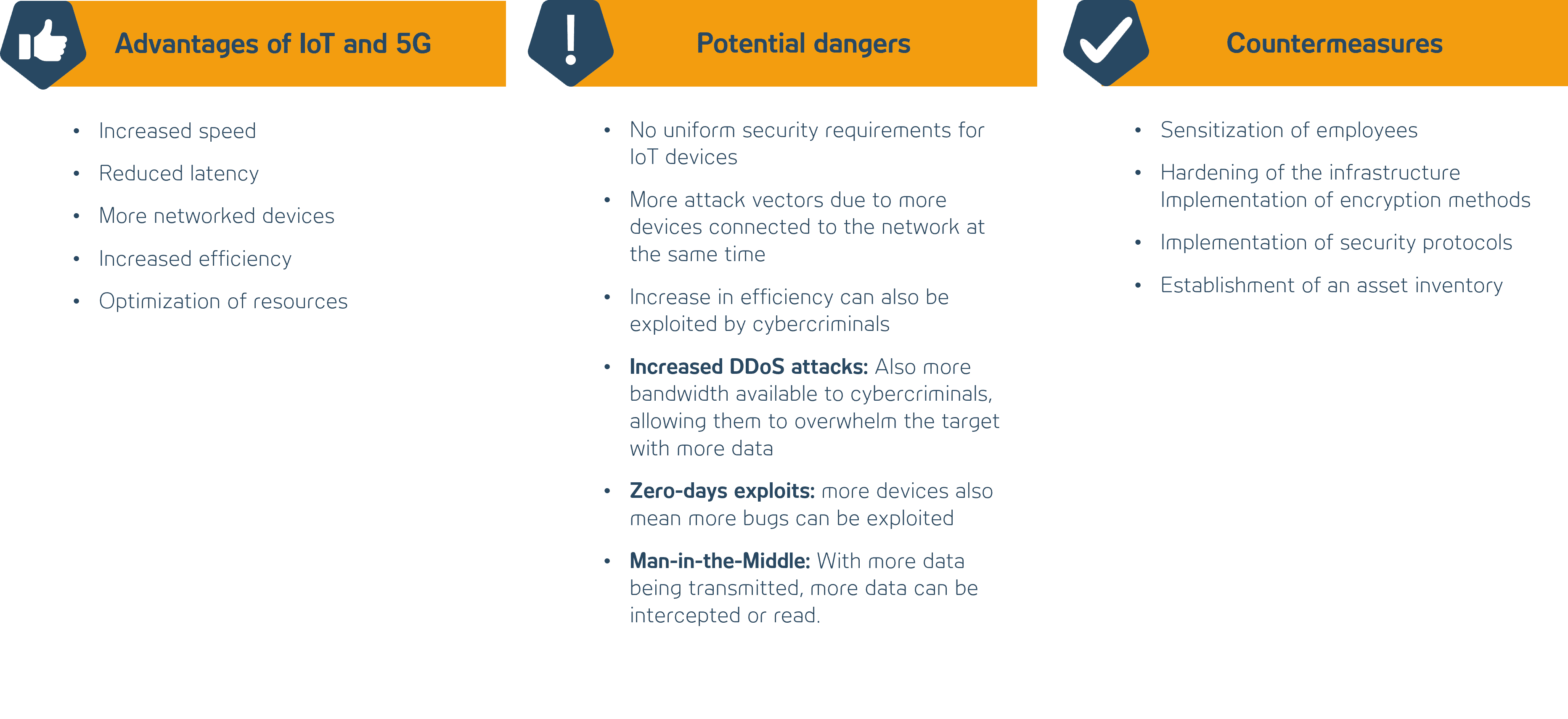
The term “Internet of Things” or IoT refers to the networking of machines, systems or devices that are connected to the Internet. Nowadays, these are no longer just computers or smartphones. These are any Internet-enabled household devices that are usually connected to the Internet via WLAN as a local network and communicate with each other, such as the self-ordering refrigerator or vehicles that exchange traffic information. Market research and consulting firm Frost & Sullivan estimates that by 2023, there will be nearly 42 billion IoT devices globally [1] exist.
But what is 5G and how does it relate to IoT?
5G stands for the 5th generation of mobile communications and is thus the successor to 4G (LTE). 5G has been available in Germany since 2019 and is to be expanded further in the future. The big advantage of 5G is its exceptionally high speed and low latency. In conjunction with the ever-growing number of IoT devices, 5G enables the high number of devices to communicate quickly without compromising network quality. 5G is therefore an essential component for the reliable and fast communication of many networked IoT devices.
Artificial Intelligence and Deep Fakes
Artificial intelligence is on everyone’s lips at the moment in view of ChatGPT. Basically, AI is based on algorithms, training data and computing power. These can increase efficiency in many areas. So AI is more than just a chatbot that can respond to questions. AI also has great potential for information security. Using AI, for example, large volumes of data can be analyzed and anomalies detected at an early stage, and potential attacks can be averted in good time. However, cybercriminals are also using AI and developing new attack methods, such as Deep Fake, which represents a new potential threat.
What is Deep Fake?
Deep Fake makes it possible to create media content that is deceptively real by means of artificial intelligence. With the help of complex algorithms, faces can be replaced in videos and voices can be imitated, for example. With improved technology, more computing power, and the constant advancement of AI, deep fakes are becoming more and more realistic and difficult to detect. At the moment, deep fakes increasingly affect politicians or celebrities, but in my opinion, this could expand to companies and private individuals over time. In this way, new attack patterns could emerge in the future or existing attack methods could be improved. Improved phishing methods could be conceivable, for example. Instead of SMS or email, phishing methods could be deceptive voice or even video calls.
Deep Fake can be divided into the following three subcategories:
Falsifying image or video content
Fake faces
Fake votes
HOMEOFFICE
Digitalization is advancing all the time and, at the latest after the Covid 19 pandemic, home offices are becoming more and more prevalent and are indispensable in many areas. The 2022 BSI status report [2] also shows that attacks are always on the rise and that the biggest gateway for cybercriminals is still humans. IT departments are thus faced with an immense challenge. More devices from different networks are logging into the corporate network. The aim is to comply with regulatory and legal requirements, while at the same time taking into account the privacy of employees and the accompanying data protection regulations.
Are you interested in information security?
More blogs and news about information security can be found here!
We are at your side!
New technological advances also always mean new dangers and risks. As a result, companies are forced to constantly adapt, develop and improve security measures. With our many years of experience in implementing regulatory requirements for IT, you can therefore rely on ADWEKO’s IT security team. From gap analysis to audit preparation, audit support and audit follow-up, we are happy to assist you in all aspects of information security. In doing so, we focus on the specific circumstances of your institute and work with you to develop a solution that is right for you. Please feel free to contact us!