Information risk management
An overview
The protection of information is essential for companies in view of the constant increase in digitalization, the growing technical processing of data and increasing threats. These threats, i.e. events with a negative impact on the company, primarily affect IT and therefore also the information stored there, e.g. exposed to cyber attacks. With XAIT and DORA, the regulator is also focusing on the identification and active management of risks. Information risk management is the central starting point for all measures relating to the identification and evaluation of assets and risks and the definition and implementation of measures. Companies should therefore find an efficient strategy with a cost-benefit analysis when dealing with risks. A holistic approach to managing the identified risks within the information security management system (ISMS) should always be chosen.

Julian Philippi
Manager in IT Security Management
Information Risk management as a holistic component of the ISMS
Traditionally, the ISMS is structured in four phases (PDCA cycle):
Fig. 1: PCDA cycle of the ISMS; Source: ADWEKO Consutling GmbH
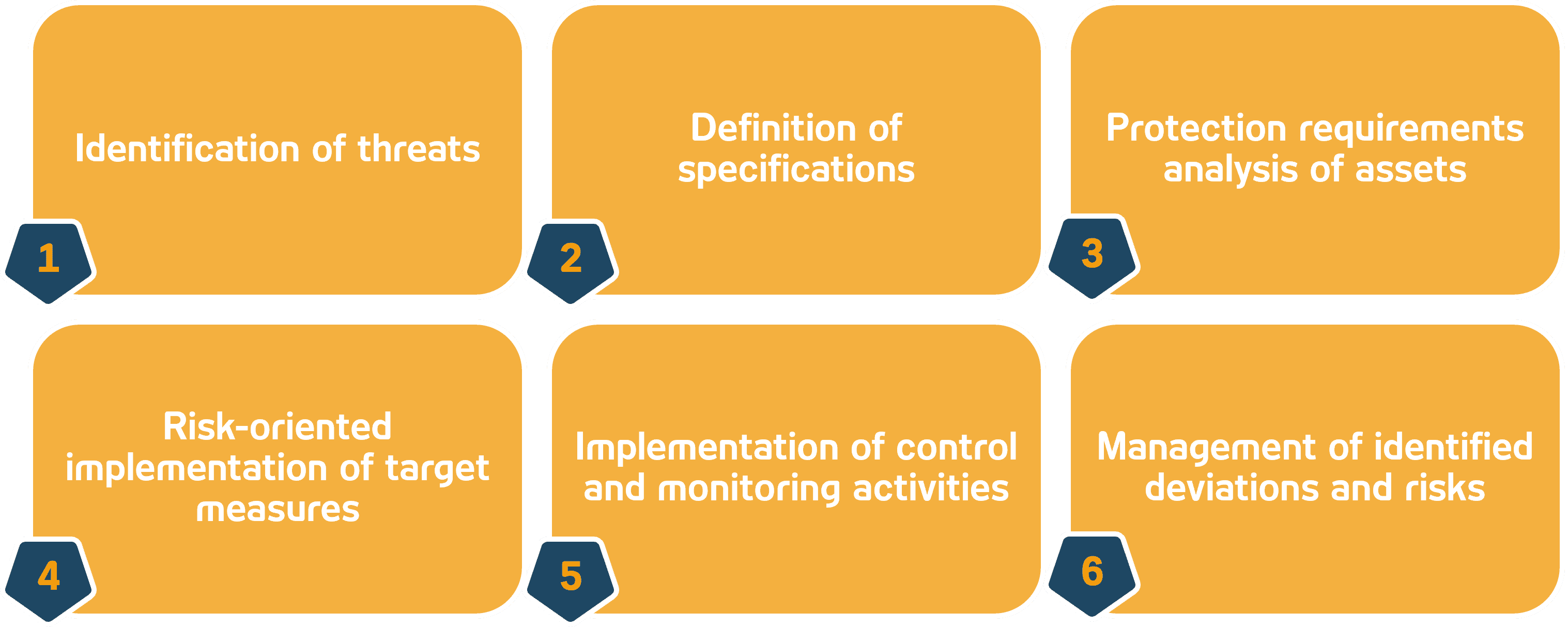
Building on this, information risk management forms the central starting point within the ISMS. This works optimally through a sequence of activities established as best practice – a summary:
Fig. 2: Tasks of information risk management; Source: ADWEKO Consutling GmbH
To protect against identified threats, specifications are defined for the various assets of the company, which form the catalog of target measures, such as is also required in the XAIT. At the same time, the information network is created, which forms the sum of all the company’s assets (e.g. information objects, processes, applications, IT systems and service providers) and maps their relationships and interdependencies. Using the information network and the relationships between the assets, the protection requirements of the assets can be determined based on the information and processes and the necessary measures can be implemented. These activities should be checked for completeness, effectiveness, appropriateness and timeliness, e.g. by means of a risk assessment are reviewed regularly and on an ad hoc basis as part of a target/actual comparison. The findings from the analysis of threats, the protection requirements of the assets and the implementation of control and monitoring activities are bundled in a holistic information risk management system and used in the risk assessment.
1 I 6 Identification of threats
When identifying threats, the individual threat situation, including the respective specifics of the institution, should be assessed. Potential hazards should be considered in order to carry out an individual assessment. For example, companies can use the BSI’s 47 elementary threats as a guide. These form a good basis for an institution-specific analysis of the threat situation and can be individually adapted or supplemented.
In addition to the information security aspects, for example Aspects from BCM are also taken into account so that the risk situation can be assessed as realistically as possible. Depending on the risk approach, various procedures can be derived from this.
In general, the economic loss and the probability of occurrence of a loss event should be assessed at this point. Whether an aggregation of different threats into scenarios or an individual analysis of the threats is carried out is institution-specific and can be decided by the institution itself. All threats should be considered and a maximum damage value, risk-mitigating measures and probability of occurrence determined for each level of consideration. When determining the probability of occurrence, the risk-mitigating measures should be taken into account for a gross-net analysis. It also makes sense to structurally identify the assets of the information network that are exposed to the respective threats.
2 I 6 Definition of specifications
The risk analysis can be used to determine which assets are exposed to which threats and which measures can be used to protect them.
The measures with which the assets of the information network are to be protected are usually defined in an institution-specific catalog of target measures. Traditionally, the 2nd Line identifies the regulatory requirements for information security and translates them into internal specifications, taking into account the state of the art. As a rule, this is based on the necessary regulatory measures and common standards such as the ISO/27000 series.
These guidelines regulate which measures should be taken to protect the institution’s information. It makes sense to base asset allocation on the results of the risk analysis in order to implement effective risk-based measures. Depending on the size of the institute, these requirements can be defined by the departments, such as authorization management or IT operations, can be broken down further. In this way, it is also possible to regulate how the target measures are to be implemented in concrete terms and the specifics of the tools used can be taken into account.
3 I 6 Protection requirements analysis of assets
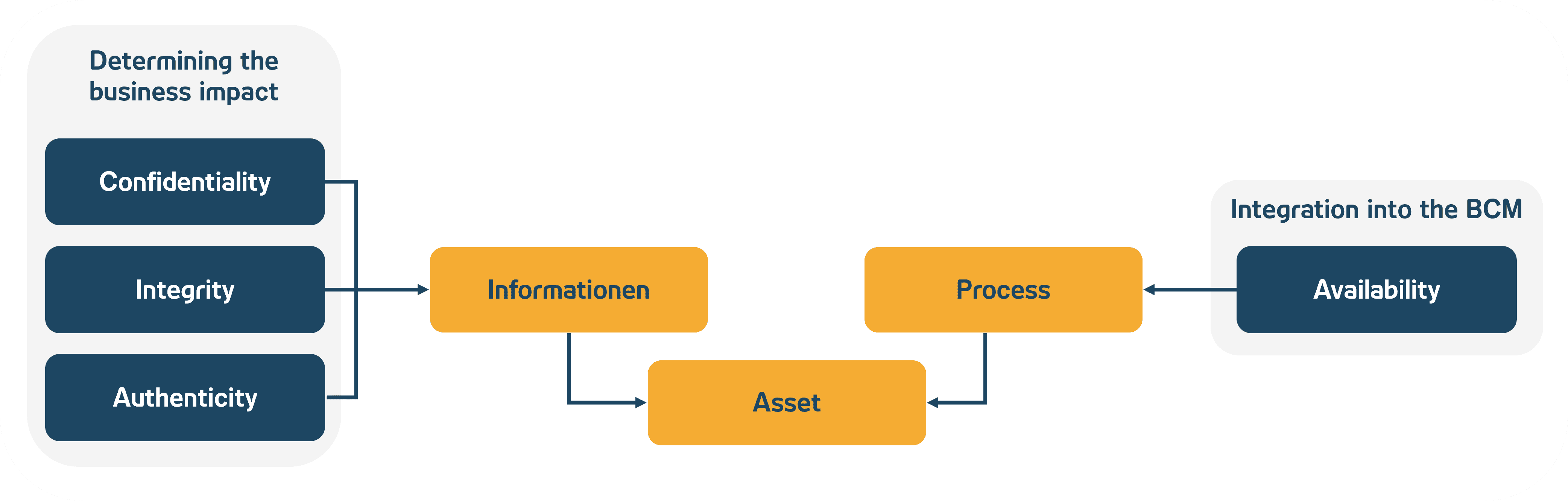
Traditionally, an institution-specific information network is set up in information security, which represents the sum of all assets belonging to the institution and, in addition to the classic IT assets (e.g. applications, IT systems or infrastructure components), also includes non-IT assets such as service providers, processes, room areas and roles as well as the institution’s information objects. To do this, all relevant assets must be identified and inventoried, so it makes sense to build on existing data sources such as the Configuration Management Data Base (CMDB) and consolidate them in the information network.
The protection requirements for the assets should be derived from the information objects (based on the protection objectives of confidentiality, integrity and authenticity) and the processes (based on the protection objective of availability). This can be based on the risk matrix and the risk categories defined there for central risk management.
Fig. 3: Determining protection requirements as the starting point for IRM; Source: ADWEKO Consutling GmbH
In order to enable a comprehensible inheritance of protection requirements from the information and processes to the other assets of the information network, the links and dependencies must be recorded as part of the structural analysis. It is recommended that an automated methodology for cascading protection requirement inheritance is mapped on the system side, which can be used, for example, for the following purposes The OSI model is used to ensure that all assets have a comprehensible protection requirement for the various protection objectives.
4 I 6 Risk-oriented implementation of the protection needs analysis
Following the definition of the information security requirements and the analysis of protection requirements, the relevant requirements should be assigned to the assets. The assignment should take into account the asset type (e.g. application, server or service provider room area) and the protection requirement for each protection objective.
Ideally, the assignment is carried out by the system and runs regularly and on an event-driven basis, e.g. in the event of changes to information security requirements or protection needs during the year. Based on this allocation, the asset manager can see which specifications are relevant for him. This ensures that the Institute’s resources can be used efficiently.
5 I 6 Implementation of control and monitoring activities
Once the information security requirements have been implemented, a review should be carried out to ensure that they have been fully and appropriately implemented. The person responsible for the asset documents whether and how the specification for the asset has been implemented. If requirements have not been implemented, these should be identified as identified and assessed in terms of their risk content/impact before they are forwarded to risk management.
Whether the implementation of the requirements is appropriate can be determined, for example, by the validated by the person responsible for the requirements in an appropriateness check. This so-called target/target comparison should be carried out annually in order to obtain an up-to-date overview of the implementation of information security requirements.
Based on the findings of the target/target comparison, a target/actual comparison is to be carried out to check the effective and current implementation of the requirements, which can be carried out, for example, as follows is required in the banking supervisory requirements for IT. Through an independent auditing body such as The 2nd line should carry out the effective and complete implementation of the specifications for the assets of the information network that have been assessed as implemented. Here too, it is advisable to agree a risk-oriented approach and not to carry out a complete annual review of all assets and requirements.
The completeness of the target/actual reconciliation should rather be achieved through automation for IT assets and over the life cycle of the assets, in which the population for the target/actual reconciliation rolls. What is specifically checked can, for example, be regulated in an audit plan, which represents one aspect of the 2nd Line control and monitoring program.
6 I 6 Management of identified deviations and risks
The deviations identified should be evaluated both qualitatively and quantitatively and incorporated into risk management via the structure of the information network. In the qualitative assessment of the deviations, the technical experts should, e.g. in IT security or authorization management. On this basis, central measures with a wide range of effects can be set up.
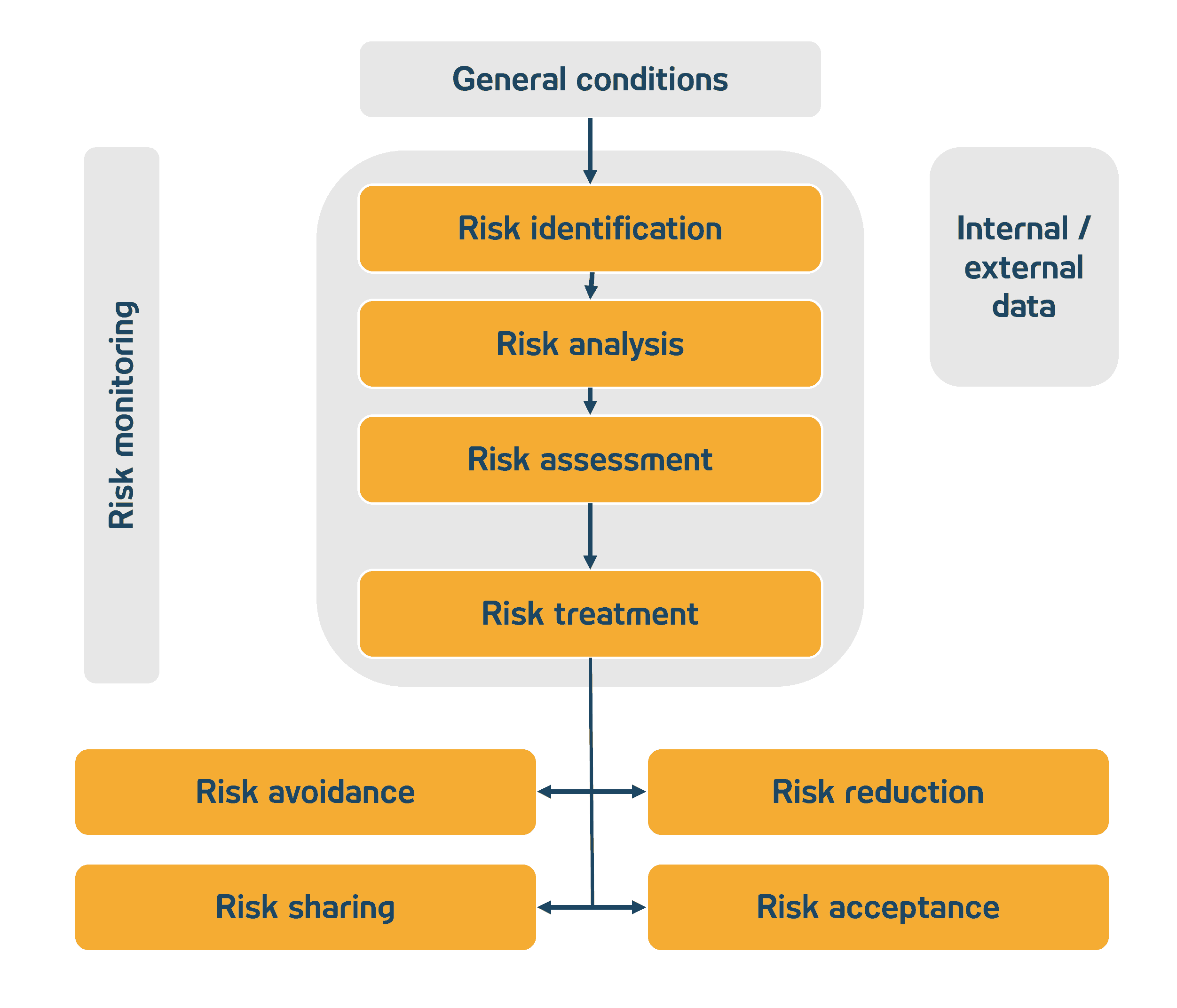
For risk assessment, aggregation at process level is a good option, as the departments responsible for this have a tangible level for assessing the extent of damage and probability of occurrence. If the results of the protection requirements analysis, the target-target and target-actual comparison and the risk analysis are stored in a system, a largely automated pre-assessment of the risks can be carried out, which then forms the basis for the final assessment by the specialist department. This also simplifies event-related risk assessment, as pre-assessed risks are updated in definable cycles and the system can react to significant changes from the hazard analysis, the target-target and target-actual comparison or the protection requirements analysis.
Fig. 4: Risk management process; Source: ADWEKO Consutling GmbH
In addition to risk assessment, the responsible department is also responsible for determining the risk strategy and, in the case of mitigation, for defining measures.
With regard to the risk measures to be defined, it is advisable to develop proposals for measures that are effective throughout the institution, have the greatest possible risk-reducing effect and can be used as a basis by the specialist departments. However, the departments are also free to define further measures. As the departments responsible for implementation often differ from the departments bearing the risk, there should be a regular exchange of information both when defining and implementing the measures. Centralized deviation management to track the implementation of measures is recommended.
We recommend a holistic process for information risk management as part of the ISMS
Information risk management offers many options for identifying, assessing and managing risks. The ISMS is structurally responsible, with operational responsibility lying with the specialist departments. It is best practice to establish a holistic process based on the four phases of the ISMS (Plan, Do, Check, Act). This should cover all aspects of risk identification, assessment and the implementation of measures. It is important to involve the specialist department and establish central processes that enable the effective management of risks and deviations.
We at ADWEKO are happy to assist you with the implementation, verification and optimization of your information risk management processes.